contents
What is Cloud Computing, Types and Examples?
What is a useful application of cloud computing?
Top 8 cloud services provider tools.
What is Amazon AWS cloud computing?
What is a Google cloud platform?
What is a Microsoft Azure Cloud Computing?
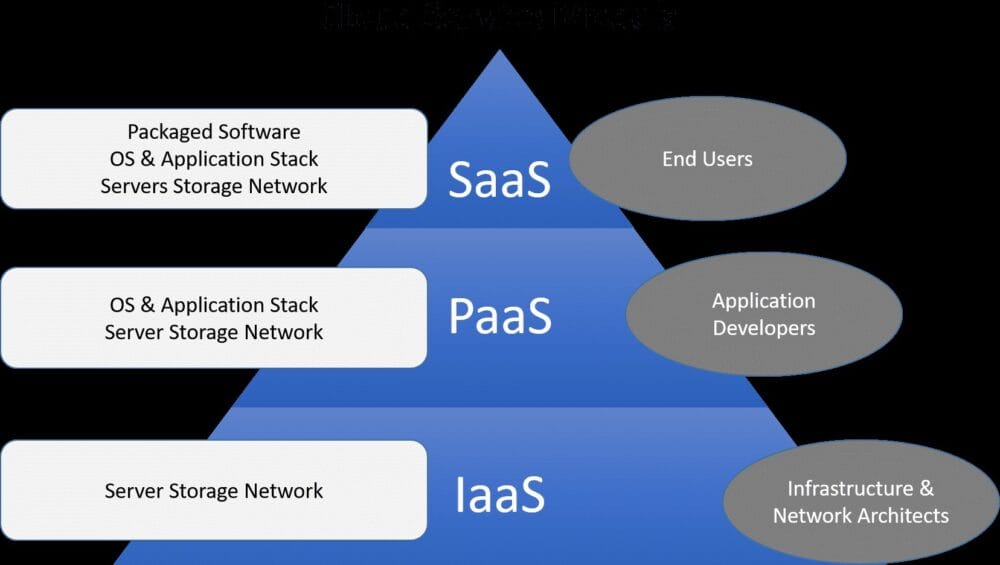
What is a (SaaS), (PaaS) and (IaaS)?
What is a Cloud computing Architecture?
What is a Amazon Elastic Compute Cloud?
What is a CI/CD pipeline AWS?
How to use cloud computing for a business.
Cloud relocations don’t occur without help from anyone else — there’s no deficiency of errands to finish before announcing the venture a triumph. Perhaps the greatest advantage of a cloud move is the chance to diminish work and working expenses. The main component is the computerization and setup of your new cloud foundation. By computerizing your cloud-based framework’s provisioning, design, and executives, your association can save time and assets for strategic development rather than routine support.
THE BEST TOOLS FOR CLOUD INFRASTRUCTURE AUTOMATION
1). AWS CloudFormation.
2). Puppet.
3). Ansible.
4). Chef.
5). Kubernetes.
6). Terraform
7). Google Cloud Deployment Manager.
8). Microsoft Azure Automation.
1). AWS CloudFormation.
AWS CloudFormation
Assisting with getting its initiative no matter what “cloud,” Amazon’s AWS CloudFormation permits you to demonstrate assets in YAML or JSON, computerize them, and afterwards send them to your AWS cloud-based foundation.
On the off chance that you use or plan to utilize AWS-based cloud contributions, CloudFormation can assist with guaranteeing setups are pretty much as simple as feasible for every one of your groups.
CloudFormation allows you to run a tremendous rundown of other AWS devices right out of the container, including Amazon CloudWatch and AWS Elastic Beanstalk. CloudFormation likewise handles computerized administration of cross-district accounts, making it simpler to venture into new regions as your business scales. CloudFormation Change Sets are an extraordinary method for reviewing approaching changes to your foundation before they occur.
2). Puppet.
Puppet.
A long-term innovator in the setup mechanization market, Puppet helps a portion of the present biggest programming groups model, design, and deliberately implement wanted arrangements of their frameworks. With Puppet Enterprise — the organization’s business offering — you can deal with all parts of your cloud-based foundation, from process to capacity to systems administration assets, at a great scope (consider upwards of 20,000 hubs for a fundamental sending). What’s more, it chips away at public, private, and mixture mists. You compose modules in Puppet’s area explicit language (DSL) that give code to the arrangements that are upheld by a specialist you introduce on every hub.
With Puppet Enterprise, you escape the-container organization and undertake based order execution and multi-gadget the board. Its GUI console makes it simple to characterize and deal with all the cloud machines you’ve sent. And keeping in mind that the Puppet DSL is known for requiring a long time to learn, the result can be tremendous.
Manikin keeps up with mixes and organizations with a key part like Microsoft, VMware, Google, and Amazon. AWS Ops work for Puppet Enterprise, for instance, gives a completely incorporated set-up of mechanization apparatuses for dealing with your cloud-based framework.
3). Ansible.
Ansible
As of late brought under the RedHat umbrella, Ansible is rapidly turning into an industry-standard in light of its not difficult to utilize, task-based foundation robotization. Ansible flaunts that you needn’t bother with a postgraduate education in software engineering to compose mechanization, setup, or organization assignments in its basic language, which you bundle in “playbooks.” Additionally, you can undoubtedly deal with all parts of your cloud framework without introducing a solitary specialist anyplace in your cloud foundation.
Key abilities of Ansible Tower (Ansible’s business offering) incorporate work booking, GUI-based stock administration, multi-playbook work processes, and an adaptable REST API that allows you to install Ansible Tower in practically any assignment based arrangement the board interaction.
Significant mixes incorporate AWS, Microsoft Azure Cloud Computing, VMware, Rackspace, Digital Ocean, and Google Cloud Computing.
4). Chef.
Chef.
Cook is one more veteran player in the framework setup game. Like Puppet, Chef gives its DSL to assist you with upholding everything from arrangement approaches to the nonstop conveyance of creation code. For Chef Automate clients (Chef’s business stage), you can mechanize the administration of your self-facilitated AWS-put together foundation concerning an hourly premise or use AWS Ops work for Chef Automate.
With Chef Automate you can expect basic highlights like itemised consistency for the executives, high accessibility, and GUI-based work process pipeline creation.
Significant reconciliations incorporate AWS, Microsoft Azure Cloud Computing, VMware, and Google Cloud Computing.
5). Kubernetes.
Kubernetes
Initially created by Google, Kubernetes is a holder coordination stage for robotizing the arrangement, scaling, and the board of containerized applications. Truth be told, it’s secured itself as the defacto standard for compartment arrangement and is the leader task of the Cloud Native Computing Foundation, upheld by vital participants like Google, AWS, Microsoft, IBM, Intel, Cisco, and RedHat.
6). Terraform
Terraform
One more part of the foundation of the board is the possibility of “framework as code.” The Big 3 all guarantee this as a focal way of thinking, and Terraform is the same. Set forth plainly, Terraform is an open-source instrument that you use to compose decisive setup records to make and change framework, yet it’s not a “design computerization device.”
7). Google Cloud Deployment Manager.
Google Cloud Deployment Manager
Assuming you intend to fabricate your cloud framework with Google Cloud Computing, look at Cloud Deployment Manager. Here you can robotize the arrangement and organization of your Google cloud with equal, repeatable organizations and format driven setups. Cloud Deployment Manager gives a rich arrangement of apparatuses from CLIs and APIs to GUIs for dealing with all periods of your framework’s design and the executives, from asset creation to cancellation.
8). Microsoft Azure Automation.
Microsoft Azure Automation
Purplish blue Automation conveys a cloud-based computerization and arrangement administration that gives predictable administration across Azure and non-Azure conditions. It comprises interaction robotization, updating the executives, and arrangement highlights intended to assist you with diminishing mistakes and cutting the time spent on your framework organizations. Sky blue Automation likewise gives mechanized command over support and consistence runs.
The best part is that it’s not only for Windows! With Azure Automation, you get heterogenous arrangements for Windows or Linux utilizing computerization that you trigger with PowerShell or Python runbooks.
Microsoft is showing its commitment to the cutting edge DevOps professional. If you want to run an assorted arrangement of working frameworks, Azure could be an incredible method for rolling.
Cisco Intelligent Automation for Cloud
Cisco gives various cloud contributions, from private to public to crossover arrangements. Close by these contributions, Cisco Intelligent Automation for Cloud gives everything from framework as-a-administration (IaaS) to involved provisioning and the executives of occurrences running in the Cisco cloud or other cloud conditions, including AWS, OpenStack, and VMware.
Top highlights incorporate a self-administration entryway for clients of your cloud, multi-occupancy, and organization administration robotization. However obviously made in light of Cisco’s cloud framework contributions, Cisco Intelligent Automation for Cloud benefits from having the option to broaden the robotization tooling into different biological systems. (Cloud computing)