contents
What is Cloud Computing, Types and Examples?
What is a useful application of cloud computing?
Top 8 cloud services provider tools.
What is Amazon AWS cloud computing?
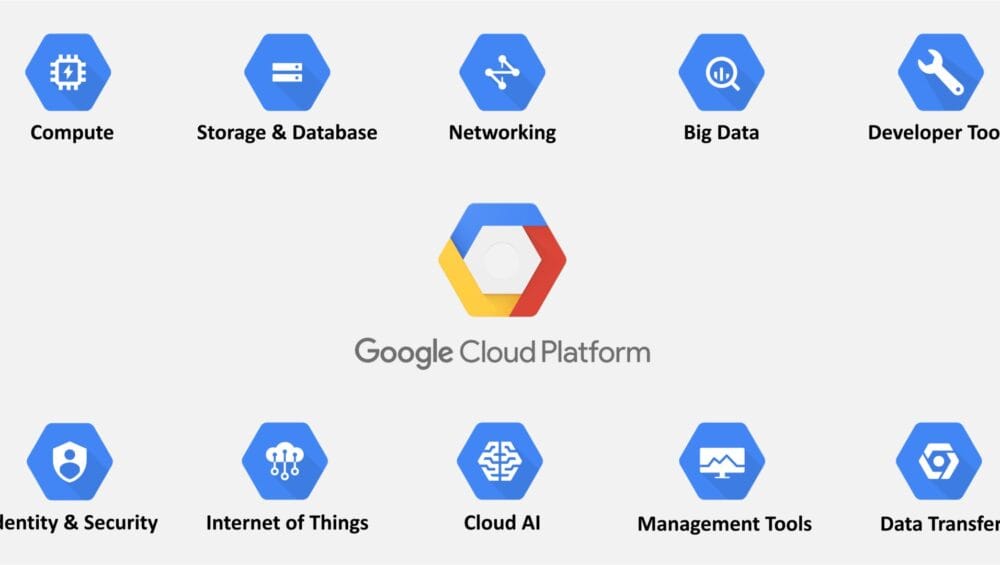
What is a Google cloud platform?
What is a Microsoft Azure Cloud Computing?
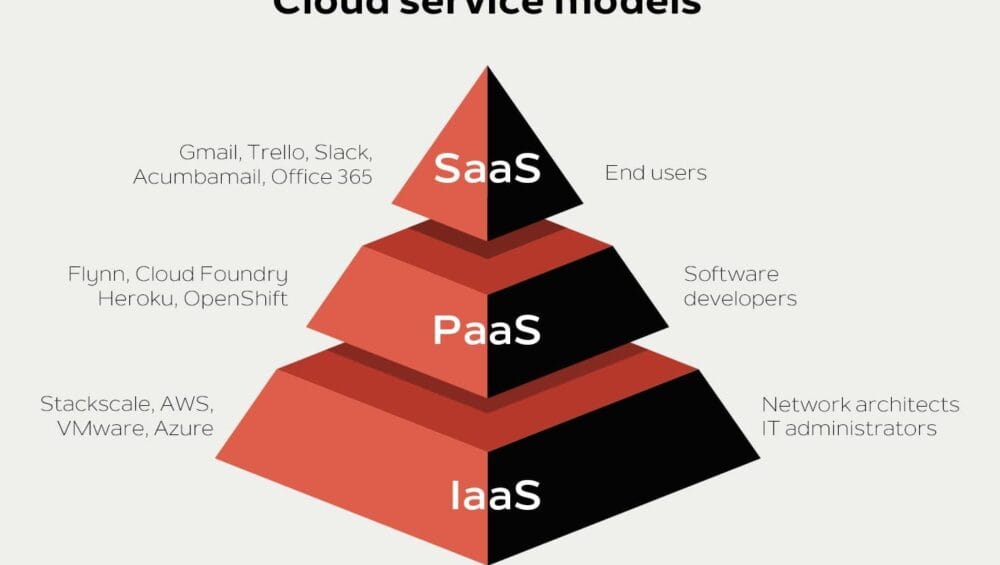
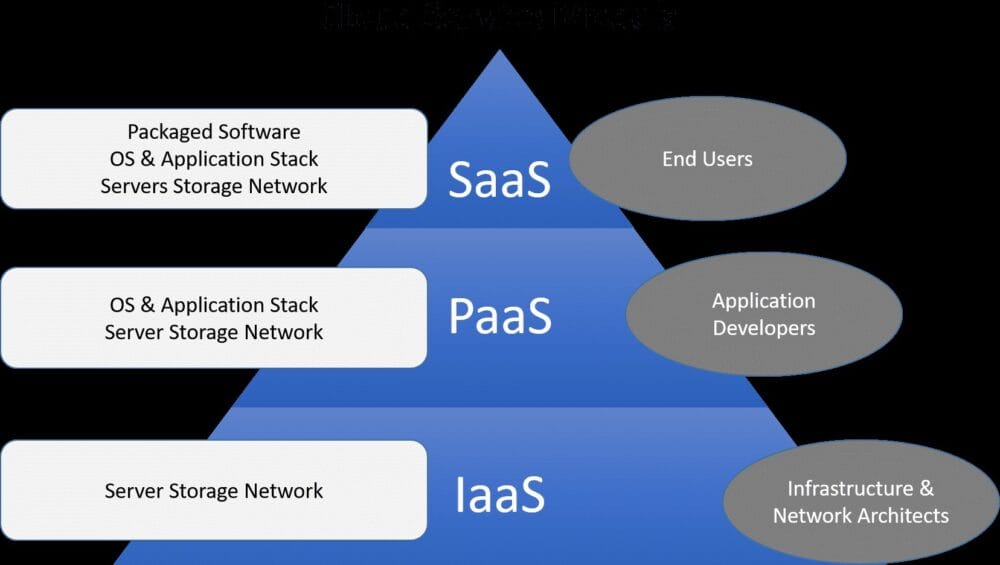
What is a (SaaS), (PaaS) and (IaaS)?
What is a Cloud computing Architecture?
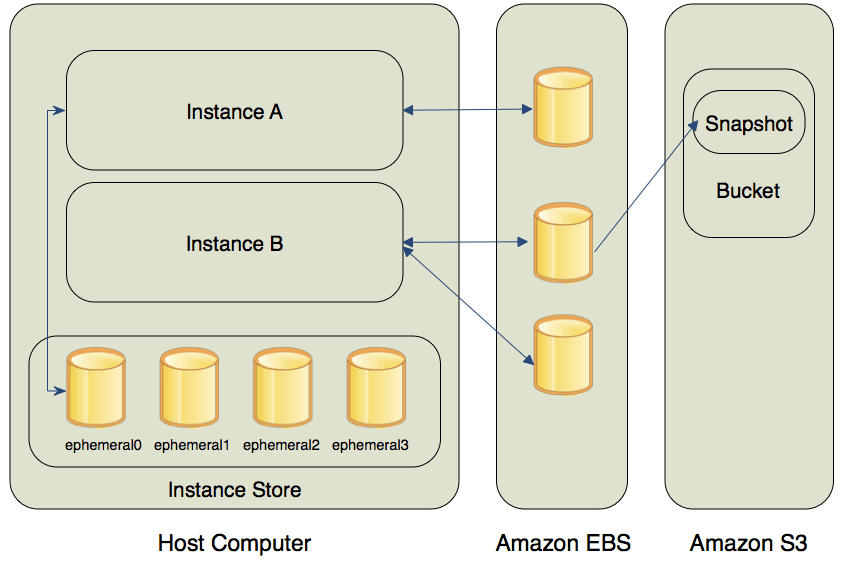
What is a Amazon Elastic Compute Cloud?
What is a CI/CD pipeline AWS?
How to use cloud computing for a business.
WHAT IS CLOUD COMPUTING?
Distributed computing permits us to store data (information, documents, pictures, sounds, and recordings) on the cloud and access this data utilizing a web association. As the cloud supplier is answerable for giving security, so they offer different reinforcement recuperation applications for recovering the lost information.
DISTRIBUTED (CLOUD) COMPUTING APPLICATION
Cloud specialist organizations give different applications in the field of workmanship, business, information capacity and reinforcement administrations, training, diversion, the executives, interpersonal interaction, and so forth.
1. Craftsmanship Applications
Distributed computing offers different craftsmanship applications for rapidly and effectively planning alluring cards, booklets, and pictures. Some most generally utilized cloud workmanship applications are given beneath:
¡. Moo
Moo is one of the most amazing cloud workmanship applications. It is utilized for planning and printing business cards, postcards, and little cards.
ii. Vistaprint
Vistaprint permits us to effortlessly plan different printed promoting items, for example, business cards, Postcards, Booklets, and wedding solicitations cards.
iii. Adobe Creative Cloud
Adobe imaginative cloud is made for planners, specialists, movie producers, and other innovative experts. It is a set-up of applications that incorporates PhotoShop picture altering programming, Illustrator, InDesign, TypeKit, Dreamweaver, XD, and Audition.
2. Business Applications
Business applications depend on cloud specialist organizations. Today, every association requires a cloud business application to develop its business. It likewise guarantees that business applications are 24*7 accessible to clients.
There are the accompanying business uses of distributed computing –
I. MailChimp
MailChimp is an email distributing stage which gives different choices to configuration, send, and save formats for messages.
iii. Salesforce
Salesforce stage gives apparatuses to deals, administration, showcasing, web-based business, and then some. It additionally gives a cloud advancement stage.
iv. Jabber
Jabber assists us with sharing significant data about the association continuously.
v. Bitrix24
Bitrix24 is a coordinated effort stage that gives correspondence, the board, and social cooperation devices.
vi. Paypal
Paypal offers the most straightforward and least demanding web-based instalment mode utilizing a solid web account. Paypal acknowledges the instalment through check cards, Mastercards, and from Paypal account holders.
vii. Slack
Slack represents a Searchable Log of all Conversations and Knowledge. It gives an easy to use interface that assists us with making public and private channels for correspondence.
viii. Quickbooks
Quickbooks deals with the wording “Run Enterprise whenever, anyplace, on any gadget.” It gives internet bookkeeping answers for the business. It permits more than 20 clients to work all the while on a similar framework.
3. Information Storage and Backup Applications
Distributed computing permits us to store data (information, documents, pictures, sounds, and recordings) on the cloud and access this data utilizing a web association. As the cloud supplier is liable for giving security, they offer different reinforcement recuperation applications for recovering the lost information.
A rundown of information stockpiling and reinforcement applications in the cloud are given underneath –
I. Box.com
Box gives a web-based climate to get content administration, work process, and joint effort. It permits us to store various documents, for example, Excel, Word, PDF, and pictures on the cloud. The fundamental benefit of utilizing box is that it gives drag and drop administration to documents and effectively coordinates with Office 365, G Suite, Salesforce, and more than 1400 devices.
ii. Mozy
Mozy gives strong internet-based reinforcement answers for our own and business information. It plans naturally back up for every day at a particular time.
iii. Joukuu
Joukuu gives the most straightforward method for sharing and tracking cloud-based reinforcement records. Numerous clients use jouks to look through records, envelopes, and team up on reports.
iv. Google G Suite
Google G Suite is one of the most mind-blowing distributed storage and reinforcement application. It incorporates Google Calendar, Docs, Forms, Google+, Hangouts, as well as distributed storage and apparatuses for overseeing cloud applications. The most well-known application in the Google G Suite is Gmail. Gmail offers free email administration to clients.
4. Instruction Applications (education application)
Distributed computing in the instruction area turns out to be extremely well known. It offers different internet-based distance learning stages and understudies data entrances to the understudies. The upside of involving the cloud in the field of training is that it offers solid virtual homeroom conditions, Ease of openness, secure information stockpiling, versatility, more noteworthy reach for the understudies, and insignificant equipment prerequisites for the applications.
I. Google Apps for Education
Google Apps for Education is the most broadly involved stage with the expectation of complimentary electronic email, schedule, records, and cooperative review.
ii. Chromebooks for Education
Chromebook for Education is perhaps the main Google venture. It is intended for the reason that it upgrades instruction advancement.
iii. Tablets with Google Play for Education
It permits teachers to rapidly execute the most recent innovation arrangements in the homeroom and make it accessible to their understudies.
iv. AWS in Education
AWS cloud gives training agreeable climate to colleges, junior colleges, and schools.
5. Amusement Applications
Media outlets utilize a multi-cloud procedure to connect with the interest group. Distributed computing offers different diversion applications, for example, web-based games and video conferencing.
I. Web-based games
Today, cloud gaming becomes quite possibly the main amusement medium. It offers different web-based games that run from a distance from the cloud. The best cloud gaming administrations are Shadow, GeForce Now, Vortex, Project xCloud, and PlayStation Now.
ii. Video Conferencing Apps
Video conferencing applications give a straightforward and moment associated insight. It permits us to speak with our colleagues, companions, and family members utilizing cloud-based video conferencing. The advantages of utilizing video conferencing are that it diminishes cost, builds effectiveness, and eliminates interoperability.
6. The board Applications
Distributed computing offers different cloud the board apparatuses which help administrators to deal with a wide range of cloud exercises, like asset arrangement, information reconciliation, and debacle recuperation. These administration apparatuses additionally give authoritative command over the stages, applications, and framework.
Some significant administration applications are –
I. Toggl
Toggle assists clients with following distributed periods for a specific task.
ii. Evernote
Evernote permits you to adjust and save your recorded notes, composing notes, and different notes in one advantageous spot. It is accessible for both free as well as a paid rendition.
It utilizes stages like Windows, macOS, Android, iOS, Browser, and Unix.
7. Social Applications
Social cloud applications permit countless clients to associate with one another by utilizing interpersonal interaction applications like Facebook, Twitter, Linkedln, and so forth.
There are the accompanying cloud-based social applications –
I. Facebook
Facebook is a person to person communication site which permits dynamic clients to share records, photographs, recordings, status, and more to their companions, family members, and colleagues utilizing the distributed storage framework. On Facebook, we will continuously get warnings when our companions like and remark on the posts.
ii. Twitter
Twitter is a person to person communication site. It is a microblogging framework. It permits clients to follow high profile famous people, companions, and family members, and get news. It sends and gets short posts called tweets.
iii. Yammer
Yammer is the best group cooperation device that permits a group of representatives to visit, and share pictures, reports, and recordings.
iv. LinkedIn
LinkedIn is an interpersonal organization for understudies, freshers, and experts.
8. Utilizations of distributed computing in Healthcare
Patients, specialists, and medical services associations all advantage of the cloud’s functional, useful, and monetary benefits.
9. GPS Application
Clients are worked with highlights like GPS which is one more progression of distributed computing and its applications. These applications assist clients with directing the bearings from the guide alongside tracking down areas on the web. Destinations, for example, google maps, yippee maps, and so on are such applications that give Cloud administrations. These applications are utilized by a large number of individuals and are allowed to utilize.
10. Bookkeeping Application
Bookkeeping programming is one of the continuous uses of distributed computing that helps the board connect with the bookkeeping portion of the business. Out and out is one such application utilized by bigger undertakings helping continuously everyday bookkeeping administration. It assists you with following constant costs, benefits, and misfortunes. Kash Flow and Zoho Books are different instances of cloud bookkeeping applications.
11. URL transformation Applications
There are a few virtual entertainment applications, out of them is a Twitter-related application that assists with changing over lengthy measured URLs in to short URLs. The reason for the application, for example, bitly is to change over the long URL into more limited ones which thusly diverts the client to the first site. It helps in microblogging and gets the application from any sort of malware and hacking movement.
12. Meeting Applications
Utilizations of Cloud Computing likewise give go-to-meeting offices, for example, video conferencing and other internet meeting applications. These are cloud application benefits that permit you to begin a gathering for individual and expert prerequisites. These associates gatherings right away and different elements like sharing introductions and screen sharing offices. ‘GoToMeeting’ and ‘Zoom’ are a portion of the applications that work with the client with all elements for smooth video conferencing.
13. Information Storage Applications
Information Storage utilization of the PC is likewise one of the choices for Applications of Cloud Computing. It is likewise one of the different cloud applications, which permits you to store data like information, records, pictures, and so forth, on the cloud. It helps access the data utilizing the cloud application. These Applications of Cloud Computing are made for security and to guarantee the information is supported safely. Information can be reestablished and changed over into different document designs which incorporate word, pdf, succeed, etc. Applications like Box, mozy, jouks and Google Suite are wonderful distributed storage models.
14. Antivirus Applications
Different antivirus applications are likewise accessible for help administration. These cloud application administrations give the smooth working of the framework. They benefit the clients in numerous ways which helps clean the framework and identify and fix dangers of malware and different types of infections. This antivirus is for nothing and is viewed as the best antivirus for your PC. The significant capacity of this application is to distinguish malware by sending the data to the server farm of the cloud and fixing something very similar. Sophos Endpoint Protection and Kaspersky Endpoint security cloud are a portion of the unmistakably utilized cloud antivirus programming. (Cloud computing)