contents
What is a Cyber security definition, type and examples?
What is a network security and type?
What is application security and types?
What is a IoT (Internet of Things) security, for example?
What is Ethical Hacking, types, and example?
Cyber security advantages and disadvantages.
What is a Basic framework network protection?
What is firewall for important cyber security?
What is a role encryption in cyber security?
What is a cyber security executive order?
Top ten future careers in cyber security.
What is a role coding in cyber security?
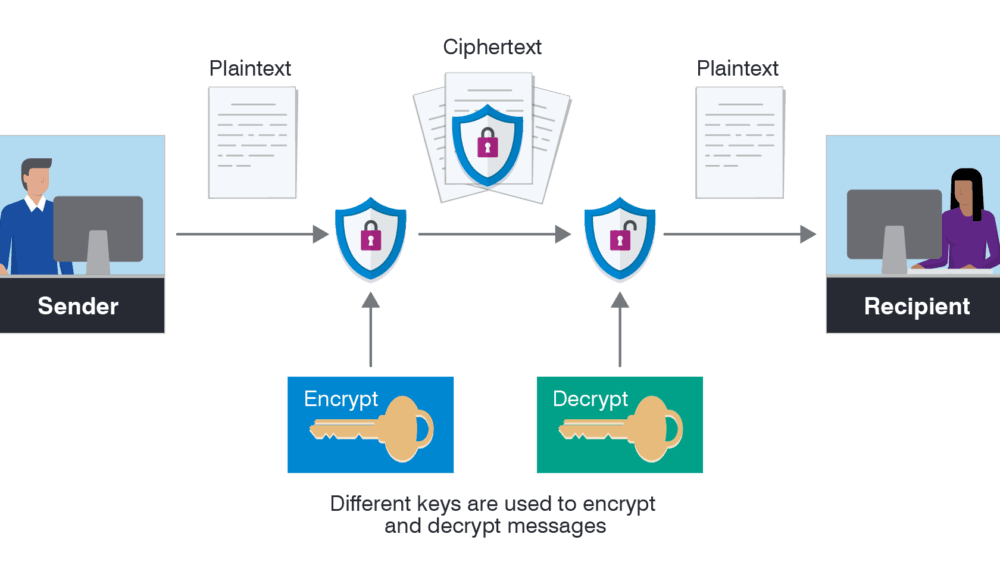
[A]. WHAT IS ENCRYPTION?
Encryption is an approach to scrambling information so that main approved gatherings can get the data. In specialized terms, it is the most common way of changing over intelligible plaintext to boundless text, otherwise called ciphertext. In more straightforward terms, encryption takes meaningful information and adjusts it so it seems irregular. Encryption requires the utilization of a cryptographic key: a bunch of numerical qualities that both the shipper and the beneficiary of a scrambled message settle on.
![]()
[B]. WHAT IS A KEY IN CRYPTOGRAPHY?
A cryptographic key is a series of characters utilized inside an encryption calculation for modifying information with the goal that it seems irregular. Like an actual key, it locks (encodes) information so just somebody with the right key can open (decode) it.
[C]. WHAT ARE THE DIFFERENT TYPES OF ENCRYPTION?
♦ The two main kinds of encryption⇒
1). symmetric encryption
2). Asymmetric encryption
1). symmetric encryption
In symmetric encryption, there is just a single key, and all conveying parties utilize something similar (secret) key for both encryption and decoding.
2). Asymmetric encryption
In lopsided, or public key, encryption, there are two keys: one key is utilized for encryption, and an alternate key is utilized for decoding.
Topsy-turvy encryption is a primary innovation for TLS (frequently called SSL).
[D]. FOR WHAT REASON IS INFORMATION ENCRYPTION IMPORTANT? ( CYBER SECURITY )
1). Privacy
2). Security
3). Data integrity
4). Authentication
5). Regulations
Privacy: Encryption guarantees that nobody can understand interchanges or information very still except the expected beneficiary or the legitimate information proprietor. This forestalls aggressors, promotion organizations, Internet specialist co-ops, and at times states from capturing and perusing delicate information.
Security: Encryption forestalls information breaks, whether the information is on the way or very still. Assuming a corporate gadget is lost or taken and its hard drive is appropriately scrambled, the information on that gadget will in any case be secure. Essentially, scrambled correspondences empower the imparting gatherings to trade delicate information without releasing the information.
Data integrity: Encryption likewise forestalls malevolent conduct, for example, on-way assaults. At the point when information is sent across the Internet, encryption (alongside other uprightness insurances) guarantees that the very thing the beneficiary gets has not been altered on the way.
Authentication: Public key encryption, in addition to other things, can be utilized in a layout where a site’s proprietor claims the private key recorded in the site’s TLS declaration. This permits clients of the site to be certain that they are associated with the genuine site (see What is public-key encryption? to find out additional).
Regulations: For this large number of reasons, numerous industry and unofficial laws require organizations that handle client information to keep that information encoded. Instances of administrative and consistence guidelines that require encryption incorporate HIPAA, PCI-DSS, and the GDPR.
[E]. WHAT IS AN ENCRYPTION CALCULATION?
An encryption calculation is a technique used to change information into ciphertext. A calculation will utilize the encryption key to modify the information in an anticipated manner so that even though the scrambled information will seem arbitrary, it tends to be turned around into plaintext by utilizing the decoding key.
[F]. WHAT ARE SOME NORMAL ENCRYPTION CALCULATIONS?
Normally utilized symmetric encryption calculations include:
AES
3-DES
SNOW
Normally utilized Hilter kilter encryption calculations include:
RSA
Elliptic bend cryptography
How is encryption used to keep Internet perusing secure?
Encryption is fundamental for an assortment of innovations, however, it is particularly significant for keeping HTTP solicitations and reactions secure, and for confirming site beginning servers. The convention liable for this is called HTTPS (Hypertext Transfer Protocol Secure). A site served over HTTPS rather than HTTP will have a URL that starts with https://rather than HTTP://, typically addressed by a got secure in the location bar.
HTTPS utilizes the encryption convention called Transport Layer Security (TLS). Before a previous encryption convention called Secure Sockets Layer (SSL) was the norm, however, TLS has supplanted SSL. A site that executes HTTPS will have a TLS testament introduced on its starting point server. Get more familiar with TLS and HTTPS.
To assist with keeping the Internet safer, Cloudflare offers free TLS/SSL encryption for any sites utilizing Cloudflare administrations. Advance more about Universal SSL from Cloudflare.
[E]. WHAT IS ENCRYPTION IN NETWORK SAFETY?
Encryption endeavours to make data muddled by any individual who isn’t expressly approved to see that information. Individuals or gadgets can be approved to get to encoded information in numerous ways, yet ordinarily, this entrance is allowed using passwords or decoding keys(cyber security)